Cyber Incident Management System
Streamline your security incident response with our advanced CIMS platform. Real-time monitoring, automated workflows, and detailed analytics to keep your organization secure.
Core Features
Comprehensive incident management capabilities to protect your organization
Real-time Monitoring
24/7 monitoring of your systems with instant alerts and notifications for any security incidents.
Incident Tracking
Detailed tracking and logging of all security incidents with complete audit trail and documentation.
Automated Response
Predefined workflows and automated actions for common security incidents to minimize response time.
Advanced Analytics
Detailed insights and reporting to improve your security posture and incident response capabilities.
Patch & Asset Management
Centralized management of system patches and assets with automated deployment capabilities for maintaining security across your infrastructure.
Identity & Access Management
Comprehensive identity and access management capabilities for enhanced security
Adaptive Authentication
Strengthen security with context-aware, multifactor authentication that adapts to user behavior and risk factors.
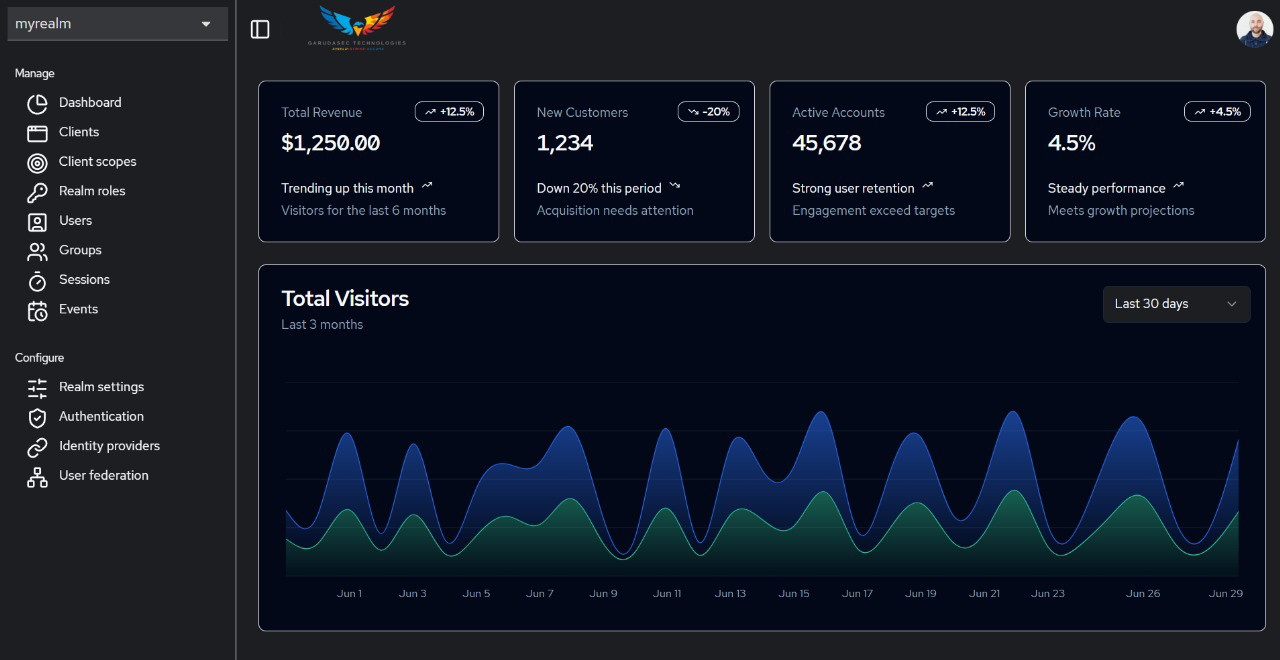
Role-based Access Control
Define and enforce precise access policies to ensure users have the right permissions based on their roles.
PII Data Encryption
Protect sensitive Personally Identifiable Information (PII) with strong encryption methods, ensuring compliance with privacy standards.
User Federation
Seamlessly integrate multiple identity sources, enabling unified authentication across different platforms.
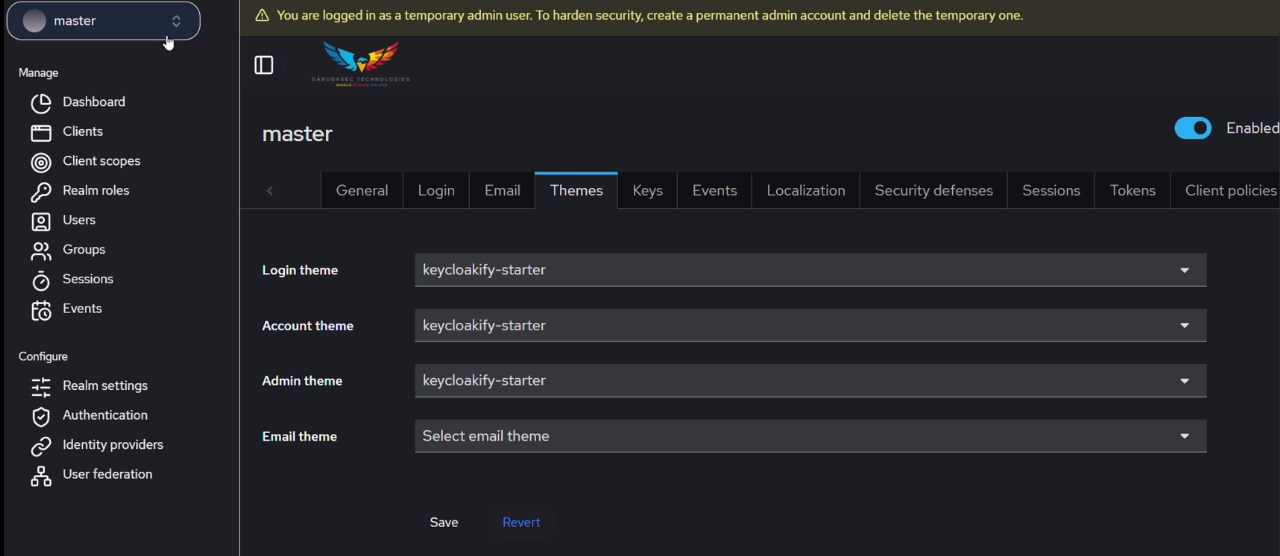
Asset and Access Management
Comprehensive protocol support and management capabilities for secure asset access and control
Protocol Support
Secure management via RDP, SSH, VNC, and TELNET protocols for comprehensive system access and control.

Instruction Management
Easily create and manage commands across multiple assets with comprehensive control and batch execution capabilities.
Batch Execution
Execute commands in bulk across multiple systems, streamlining operational processes and improving efficiency.
Session Management
Monitor, control, and disconnect live sessions in real-time. View screen recordings for post-session auditing and analysis.

Asset Tags
Implement asset identification and categorization for streamlined tracking and efficient management.
Asset Authorization
Ensure access to assets is granted only to authorized users with precise control and monitoring.
Login Policy
Enforce comprehensive login policies to enhance security and maintain access control standards.
Scheduled Tasks
Automate operations with task scheduling for better resource management and efficiency.

Vulnerability Assessment
Comprehensive scanning and analysis to identify and address security vulnerabilities
Comprehensive Scanning
Advanced detection of vulnerabilities across operating systems, network devices, applications, databases, and cloud environments.

Intelligent Detection
Advanced analysis combining signature-based and behavioral detection to identify known and zero-day vulnerabilities.
Risk-Based Prioritization
Contextualizes vulnerabilities based on asset criticality and exploitability for efficient remediation.
Patch Manager
Centralized patch management with automated deployment and rollback capabilities for efficient updates.

Ready to Enhance Your Security?
Join thousands of organizations that trust our CIMS platform for comprehensive security management.